So You've Got the Dreaded CryptoLocker. Now What?
CryptoLocker and other strains of ransomware are infecting millions of computers. How can you treat it, and how can you prevent it in the future?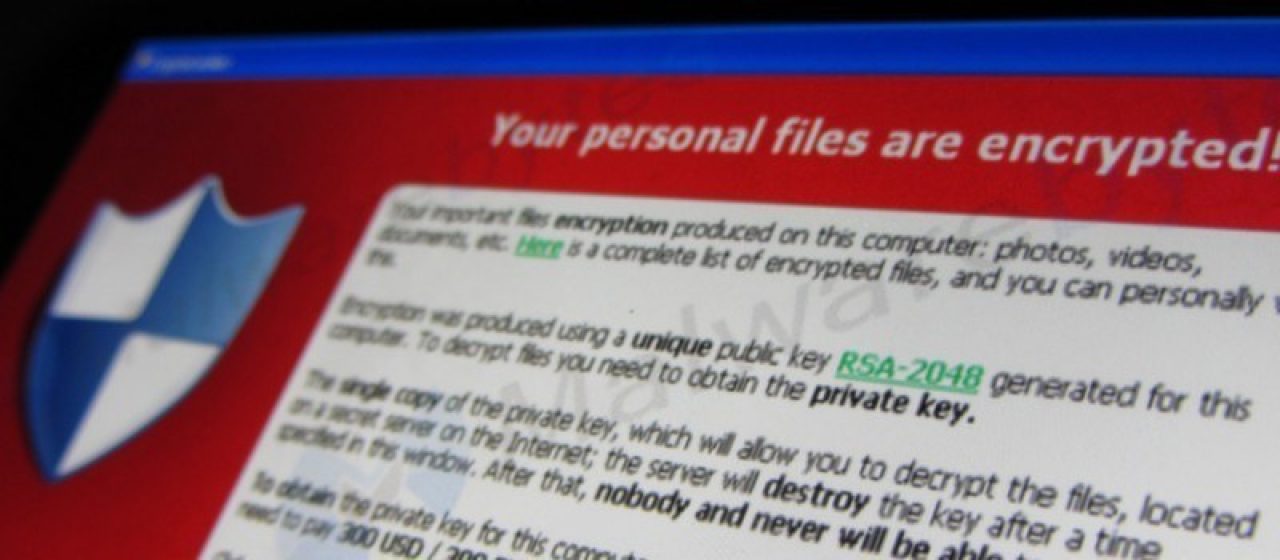
In recent weeks, we've talked about how to detect and avoid various tech support scams online. Prevention is the best defense, but we'd be kidding ourselves to pretend that any computer is immune from all malware. No matter how strong your antivirus is or how safely you browse the Web, accidents happen. The first thing to understand is this: It is not your fault. It can (and does) happen to anyone.
In this post, we'll provide real and honest advice for what to do if you've been hit by CryptoLocker. In the vast majority of cases, there is no fairytale ending. But knowing what to expect can make easier to get through this difficult event with as little damage as possible.
What Is CryptoLocker?
When we say "CryptoLocker," we are referring to a specific strain of ransomware. Ransomware, regardless of name, will follow a similar structure and work in much the same way. Common strains of ransomware include:
- CryptoLocker
- TorrentLocker
- CryptoWall
- Reveton
- KeRanger
- TeslaCrypt
- Locky
The advice in this post will be applicable to various strains of ransomware, not just CryptoLocker.
How CryptoLocker Works
Like many viruses, CryptoLocker gets into your computer via malicious downloads and email attachments. Once it's in, it will encrypt all the files on your device, rendering them completely inaccessible. Without a special encryption code, those files will be locked and lost forever.
You'll likely see a pop-up or message on your lock-screen announcing the presence of CryptoLocker. The message will include instructions on how to pay the hackers to unlock your files. There's often a time limit involved, which heightens your sense of urgency so you can't take the time to make an informed decision.
Prices vary, with the average range between $300 and $600. To protect their anonymity, hackers often demand payment in Bitcoin, a digital currency. Worse, they might ask for your credit card details, which leaves you vulnerable to theft.
The hackers who create ransomware have one singular goal in mind: to make money. They traffic in fear and confusion; the fact that you could lose invaluable photos and documents means nothing to them, except that it motivates you to pay up. The best way to defeat these criminals is to cut off the money. If you have no reason to pay them, they're out of a scam.
What Are My Options?
Well, here's where it might get discouraging. Your outcome will depend heavily on what precautions you took before getting infected.
If you have data backup...
If you have your data backed up somewhere (e.g. an external hard drive or an online cloud service), you're in luck. All of your files can be restored after your computer is wiped clean. Depending on the date of your last backup, you might lose some stuff. For example, if you back up weekly, you might lose a few days of file changes. But that's a heck of a lot better than losing everything.
If you don't have data backup...
Oh boy. Without the unique code required to unlock your files, there's no surefire way in. If you don't have extra copies of your files stored elsewhere, they might be lost to you now.
Can't tech support get rid of it?
Not often. Due to its use of encryption, the odds of decrypting (breaking) ransomware are very low. There are good developers out there who dedicate their time to decoding and breaking ransomware, but as soon as they figure one out, the bad guys release another. Here is a recent example where a security researcher was able to break a strain of ransomware called TeslaCrypt.
At the end of the day, no matter who you approach for help, you have two choices. You can pay ransom to the hackers and pray that they send you the correct decryption code to unlock your computer... or you can wipe your computer and start over.
Does Paying the Ransom Work?
In the vast majority of cases, it does. As strange as it sounds, these hackers have a reputation to defend. If word got around that paying the ransom doesn't work, no one would pay anymore. So, it's in their best interest to keep their word.
Law enforcement officials have taken the general stance that, if at all possible, you should avoid paying off these criminals. But, if you have irreplaceable photos, videos or other files, you may feel like you have no choice but to pay up. No one can make that decision but you. Be advised that paying the ransom isn't always as easy as it sounds, as discovered by this writer at The New York Times.
Learn from CyptoLocker, Take Precautions Today
Being hit with ransomware really sucks. It's scary, intimidating and upsetting to have your property violated in such a way. But, as with any mistake, you can learn from it and move forward.
The best precautions you can take are:
- Backing up your data regularly with a service like Bask Data Backup.
- Protecting your computer from malware with a strong antivirus like Trend Micro Titanium.
- Updating your software and operating system regularly to patch security loopholes.
- Follow safe Internet practices to avoid unrecognized downloads and malicious email attachments.
- Intermediate/Advanced Users: You can also try this free Bitdefender tool that can prevent many strains of ransomware from infecting your computer.
If you would like help with any of these precautions, please give us a call! We are always happy to do anything we can and to provide peace of mind. Our highest hope is that you never have to deal with this situation in the first place, and our memberships are designed to prevent it from happening now or ever again.
Each week, Bask sends educational content to our thousands of members and email subscribers. Improve your technology know-how with tips, tricks, history, news and more by signing up for our newsletter today!

 Member Connect
Member Connect